WireTap:
Breaking Server SGX via DRAM Bus Interposition
Intel's Software Guard eXtensions (SGX) is a hardware feature in Intel servers that aims to offer strong integrity and confidentiality properties for software, even in the presence of root-level attackers. To put it simply, even if the server is hacked and taken over by root-level attackers, it should be impossible to extract data that is protected by SGX. Thus, given its strong security guarantees, SGX is used by many systems to protect sensitive customer data such as cryptocurrency transactions and private messages.
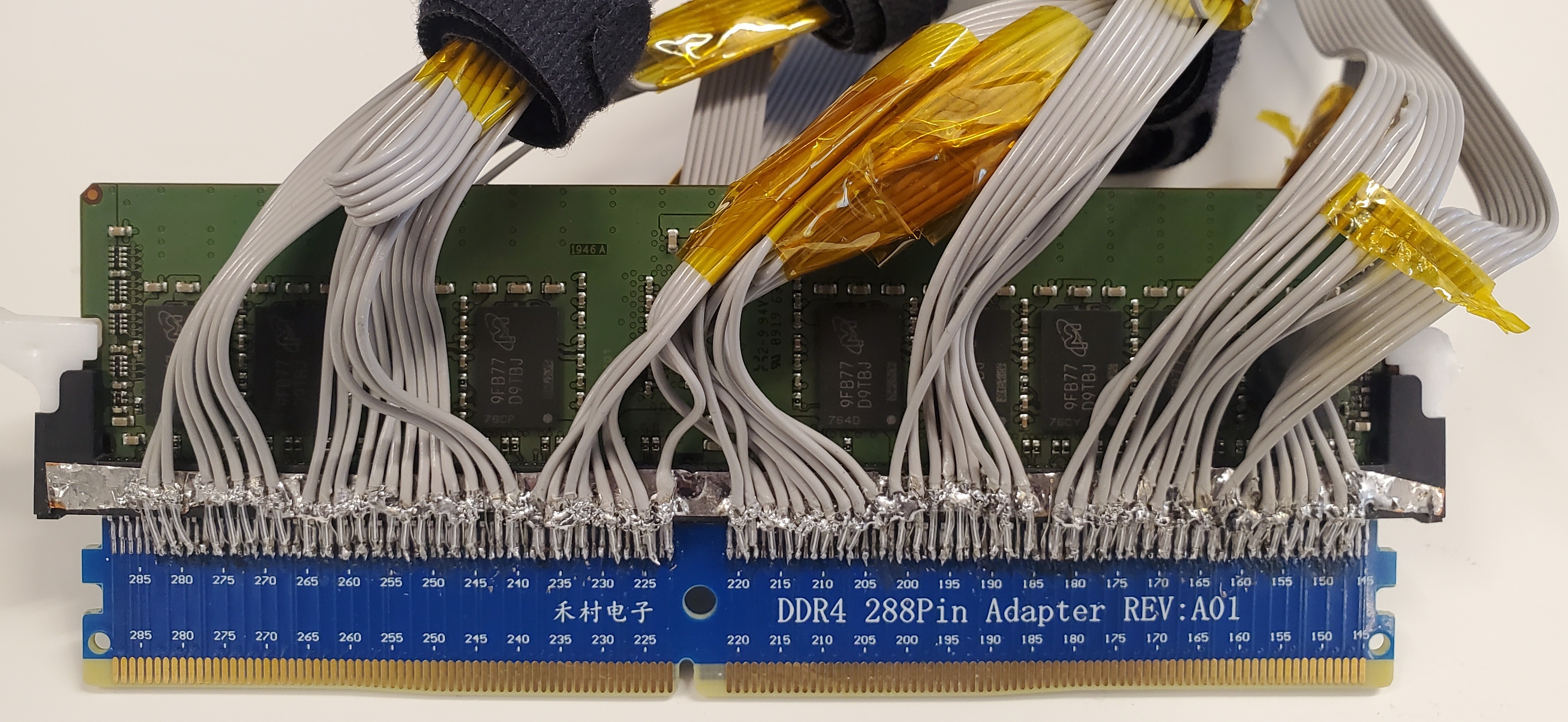
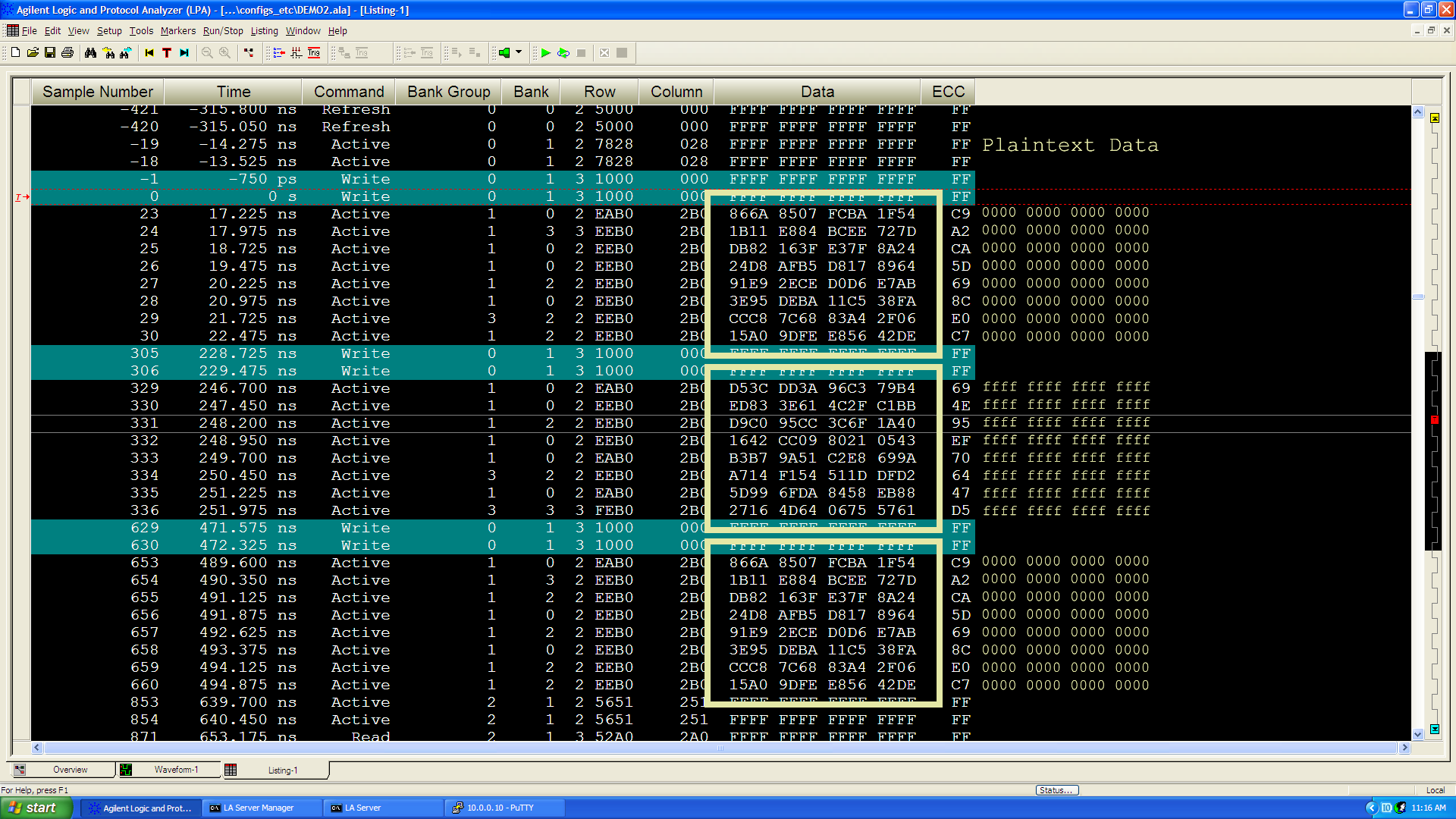
In this work we show that SGX is not impervious. More specifically, we show how one can build a device to physically inspect all memory traffic inside a computer cheaply and easily, in environments with only basic electrical tools, and using equipment easily purchased on the internet. Using our interposer device against SGX's attestation mechanism, we are able to extract an SGX secret attestation key from a machine in fully trusted status, thereby breaching SGX's security.
Finally, we study the real world implications of such breaches on SGX-backed blockchain deployments. Here, we show end-to-end attacks on both confidentiality and integrity guarantees of deployments with multi-million dollar market caps, allowing attackers to disclose confidential transactions or illegitimately obtain transaction rewards.